Healthcare networks face a fundamental shift in how they protect patient data. The proposed HIPAA Security Rule updates transform network segmentation from a recommended best practice into a mandatory compliance requirement, with explicit technical standards that auditors will verify.
This guide walks through the complete HIPAA 2.0 network design framework, from understanding what changed in the Security Rule to implementing compliant segmentation, encryption, and monitoring across your healthcare environment.

A modern HIPAA 2.0 network design framework builds on zero-trust principles, mandatory network segmentation, and automated security controls that protect electronic protected health information (ePHI). Aligned with NIST SP 800-66r2 guidance, the framework prioritizes isolating sensitive data workloads, implementing multi-factor authentication, and maintaining continuous risk monitoring to meet evolving 45 CFR 164.312 requirements.
Network segmentation works by dividing healthcare infrastructure into smaller, isolated zones. Clinical systems sit in one segment, administrative systems in another, and guest WiFi in yet another. If an attacker compromises one zone, segmentation prevents lateral movement into areas containing patient data.
Core components of the HIPAA 2.0 network framework include:
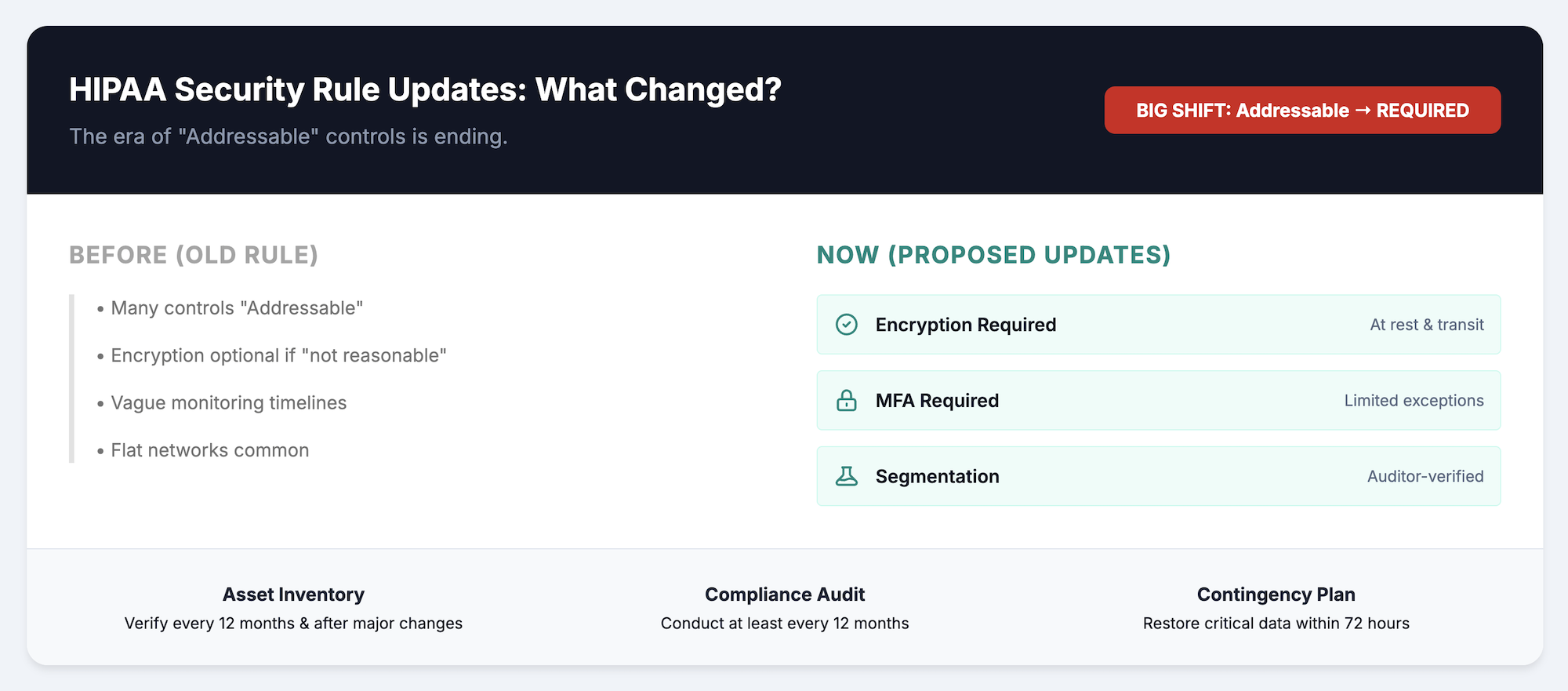
The proposed HIPAA Security Rule updates represent the most significant changes to healthcare network requirements in two decades. The original rule allowed flexibility in how organizations implemented safeguards, treating many controls as “addressable” rather than required. The updated framework moves toward explicit, mandatory controls, particularly around network architecture.
| Requirement Area | Original Rule | Updated Framework |
|---|---|---|
| Network Segmentation | Addressable (optional based on risk) | Mandatory under 45 CFR 164.312(a)(2)(vi) |
| Encryption | Addressable | Required for all ePHI transmission |
| Multi-Factor Authentication | Not specified | Explicitly required |
| Risk Assessment Frequency | Periodic | Annual minimum with continuous monitoring |
| Vulnerability Scanning | Not specified | Regular scanning required |
The shift from “addressable” to “required” changes compliance significantly. Organizations can no longer document why they chose not to implement certain controls. Network segmentation, once considered a best practice, becomes a compliance baseline that auditors will verify.
Hospitals, clinics, physician practices, health plans, and healthcare clearinghouses fall under direct HIPAA jurisdiction. Covered entities bear primary responsibility for designing and maintaining compliant network infrastructure that protects patient information throughout its lifecycle, from creation through storage and eventual disposal.
Any organization that handles ePHI on behalf of a covered entity inherits network compliance obligations through Business Associate Agreements (BAAs). Billing companies, cloud service providers, IT vendors, and even shredding services that handle paper records all qualify as business associates. The updated framework holds business associates to the same technical standards as covered entities.
Managed service providers supporting healthcare clients design and maintain compliant networks as part of their service delivery. This responsibility extends to ensuring proper segmentation, monitoring, and access controls across all client environments where ePHI resides. IT GOAT’s U.S.-based SOC and compliance teams specialize in building and maintaining healthcare networks that meet current and proposed HIPAA requirements.
The Security Rule organizes requirements into three safeguard categories. Each category influences network design decisions in different ways, and together they create a comprehensive protection framework.
Risk analysis forms the foundation of compliant network architecture. Organizations document all systems that store, process, or transmit ePHI, then assess vulnerabilities and implement appropriate controls based on identified risks. Workforce training ensures staff understand their role in maintaining network security. Written policies govern everything from access provisioning to incident response procedures.
Network hardware requires physical protection that complements technical measures. Server rooms with controlled access, workstations positioned to prevent unauthorized viewing, and secure disposal procedures for decommissioned equipment all fall under physical safeguards. A firewall cannot stop someone who walks into an unlocked server room.
Technical safeguards directly shape network architecture and represent the core of HIPAA network security requirements:
Start by identifying every system, application, and device that touches ePHI. This inventory becomes the foundation for segmentation decisions. A thorough asset inventory helps prioritize security investments based on actual risk rather than assumptions about where sensitive data lives.
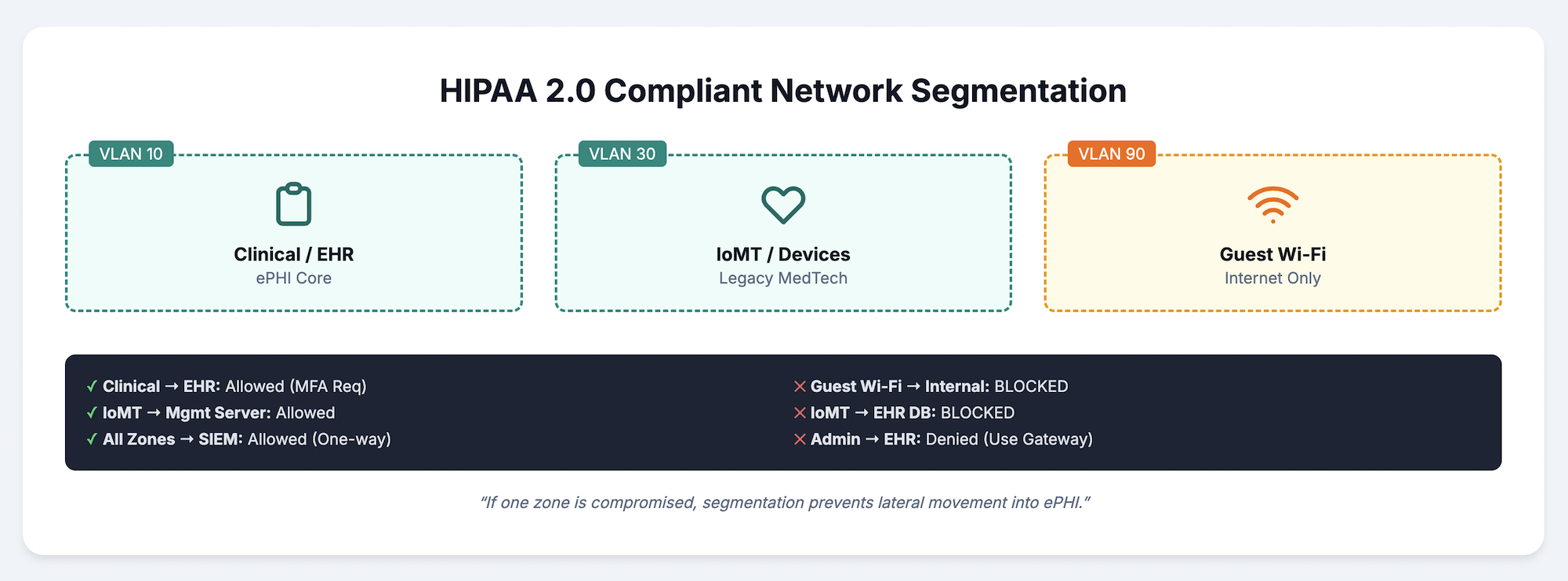
Logical separation creates boundaries between different system types. Clinical systems containing ePHI occupy isolated segments, while administrative systems, guest WiFi, and medical devices each receive their own zones. Controlled interconnection points allow necessary communication while limiting exposure.
Perimeter and internal firewalls enforce segmentation policies. Intrusion detection and prevention systems monitor for suspicious activity and can automatically block threats. Look for solutions offering stateful inspection, application-layer filtering, and integration with threat intelligence feeds that track healthcare-specific attacks.
TLS 1.2 or higher protects data moving across networks. AES-256 encryption secures stored ePHI in databases and file systems. Encryption extends to backups, mobile devices, and any cloud services handling patient information.
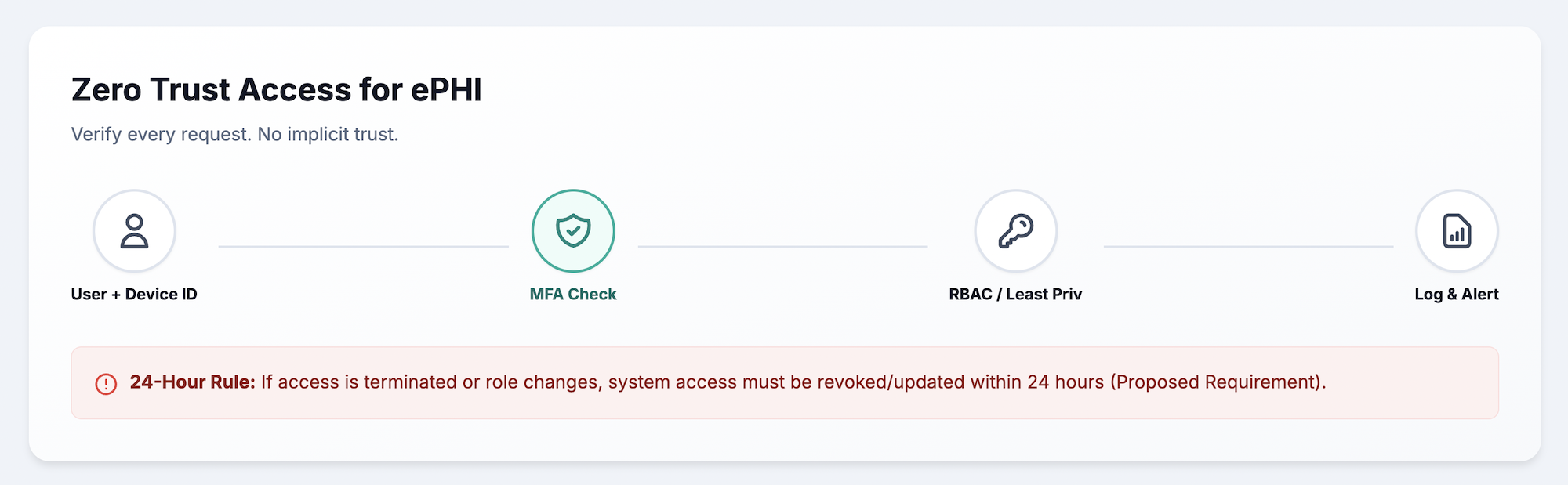
Centralized identity management with multi-factor authentication ensures only authorized users access specific network segments. Least-privilege principles limit access to the minimum necessary for job functions. A billing clerk does not require access to clinical systems, and a nurse does not require access to financial databases.
Written policies document network architecture decisions, access procedures, and security configurations. Regular training reinforces staff responsibilities and keeps security awareness current. Documentation also provides evidence during compliance audits.
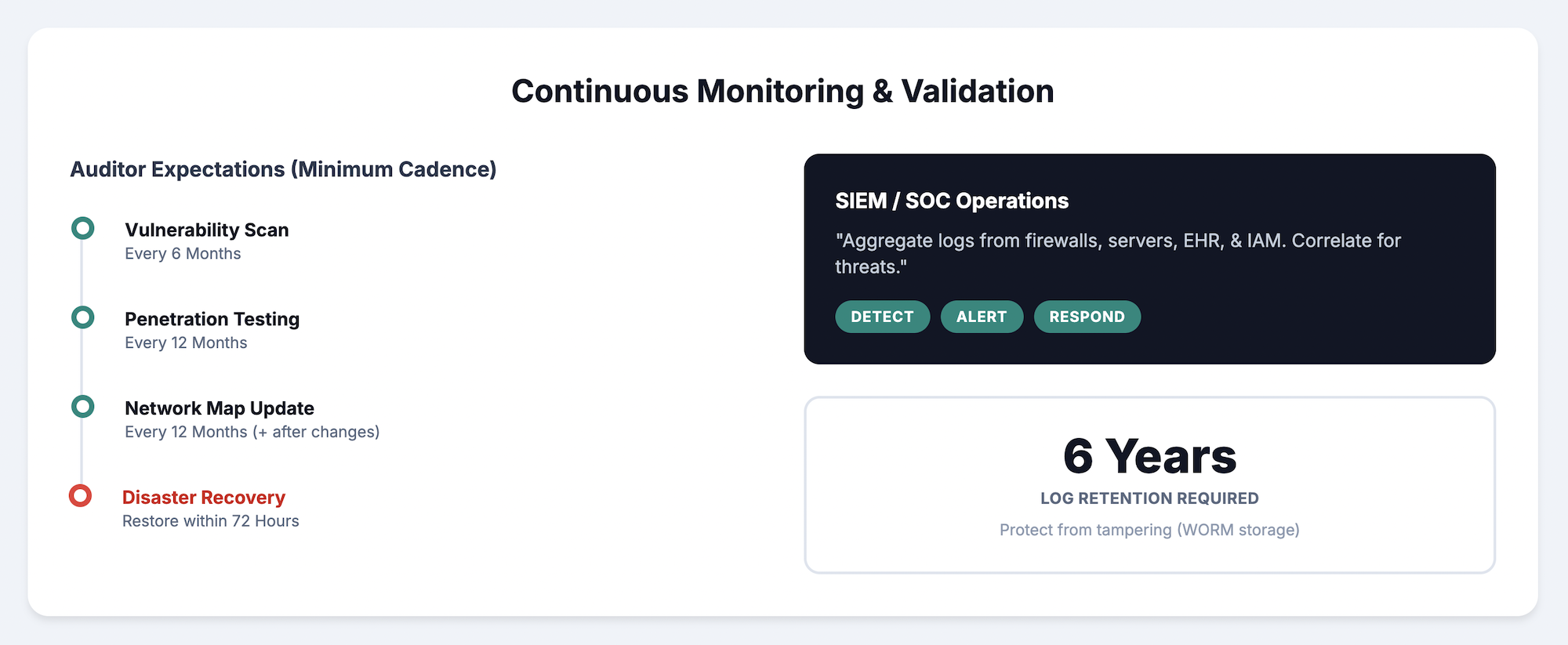
Penetration testing, vulnerability scanning, and configuration audits verify that implemented controls work as intended. Ongoing validation catches configuration drift before it becomes a compliance gap or security vulnerability.
Modern healthcare firewalls examine traffic at multiple layers. Stateful inspection tracks connection states, remembering which internal systems initiated outbound connections. Application-layer filtering inspects the actual content of traffic, catching threats that simple packet filtering misses.
IPS functionality actively blocks detected threats rather than simply generating alerts. Integration with healthcare-specific threat intelligence feeds improves detection of attacks targeting medical systems and patient data. Threat actors increasingly target healthcare organizations, making current intelligence valuable.
Redundant firewall configurations prevent single points of failure that could disrupt clinical operations. If one firewall fails, traffic automatically routes through the backup. Comprehensive logging captures all traffic decisions, providing the audit trail that compliance audits require.
Zero trust architecture assumes no user or device deserves automatic trust, even inside the network perimeter. Traditional security models trusted everything inside the firewall. Zero trust verifies every access request regardless of where it originates.

Virtual LANs isolate EHR systems from general network traffic, limiting exposure if other segments experience compromise. Proper VLAN configuration includes access control lists governing inter-VLAN communication. Traffic between VLANs passes through firewalls that enforce security policies.
Microsegmentation extends isolation to individual workloads, creating security boundaries around specific applications rather than just network segments. A compromised workstation in the billing department cannot reach the EHR database server even though both sit on internal networks. Software-defined approaches enable dynamic policy enforcement that adapts to changing conditions.
Patient and visitor WiFi operates completely isolated from clinical systems with no route between them. Administrative networks handling billing and scheduling remain separate from clinical segments. Controlled access points exist only where necessary data exchange occurs, and firewalls monitor all traffic crossing segment boundaries.
Connected medical devices present unique challenges. Many run outdated operating systems that cannot be patched. Some lack built-in security features entirely. Network isolation becomes the primary protection strategy when devices themselves cannot be secured.
Containment approaches include dedicated VLANs for medical devices, strict firewall rules limiting communication to necessary endpoints, and enhanced monitoring to detect anomalous behavior. Compensating controls address risks that device limitations prevent addressing directly.
Common IoMT categories requiring isolation:
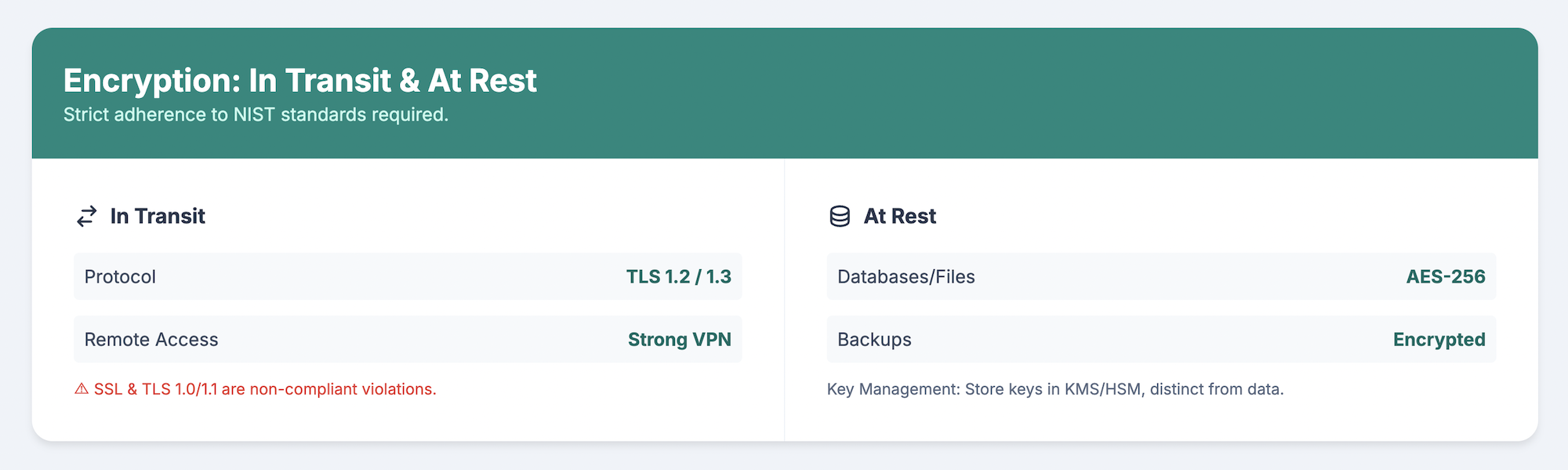
All ePHI transmission uses TLS 1.2 or 1.3 encryption. Older protocols like SSL and TLS 1.0 contain known vulnerabilities and do not meet current requirements. Remote access occurs through properly configured VPN connections with strong authentication, never through unencrypted channels.
Databases containing ePHI implement AES-256 encryption at rest. This protection extends to backups, archives, and any storage media that might leave organizational control. If a backup tape goes missing, encryption renders the data unreadable without the encryption keys.
Identity and access management platforms provide single-source authentication across network segments. Multi-factor authentication applies to all ePHI access, combining something users know (password) with something they have (phone or token). Role-based permissions ensure users access only what their responsibilities require.
Security information and event management platforms aggregate logs from across the network. SIEM systems correlate events to identify potential threats that individual log sources might miss. Integration with security operations centers enables 24/7 monitoring and rapid response when threats emerge.
HIPAA requires maintaining audit logs for six years minimum. Logs capture user access, system changes, and security events with sufficient detail to reconstruct activities during investigations. Tamper-evident logging prevents attackers from covering their tracks by modifying log files.
Documented response procedures ensure consistent, effective action when incidents occur. Playbooks specify who to contact, what systems to isolate, and how to preserve evidence. Regular tabletop exercises and simulations validate that teams can execute plans under pressure before a real incident tests them.
| Factor | Greenfield (New Build) | Brownfield (Retrofit) |
|---|---|---|
| Complexity | Lower since design starts fresh | Higher due to existing system constraints |
| Timeline | Predictable with clear milestones | Variable based on legacy dependencies |
| Cost Profile | Higher upfront, lower ongoing | Lower upfront, potentially higher ongoing |
| Segmentation Options | Full flexibility in architecture | Limited by existing infrastructure |
Most healthcare organizations face brownfield challenges, retrofitting compliance into networks built before current requirements existed. Success requires careful planning, phased implementation, and sometimes creative solutions to work within infrastructure constraints while achieving compliance goals.
Designing and maintaining HIPAA-compliant network architecture requires specialized expertise that many healthcare organizations lack internally. IT GOAT provides U.S.-based security operations, proactive monitoring, and deep compliance experience to help healthcare organizations build networks that protect patient data while supporting clinical operations.
Our team understands both the technical requirements and the practical realities of healthcare IT environments. Whether you are building new infrastructure or retrofitting existing systems, we can help you achieve compliance without disrupting patient care.
Book a consultation to discuss your HIPAA network compliance requirements.
The compliance timeline depends on when HHS finalizes the proposed Security Rule updates. Covered entities typically receive a defined implementation period, often 180 days to one year, after the final rule publication. Smaller organizations sometimes receive extended timelines to accommodate limited resources.
NIST SP 800-66 provides detailed guidance for implementing HIPAA Security Rule requirements, mapping security controls to specific HIPAA provisions. Many organizations use the NIST Cybersecurity Framework to structure their overall compliance programs, treating it as an operational roadmap for meeting regulatory obligations.
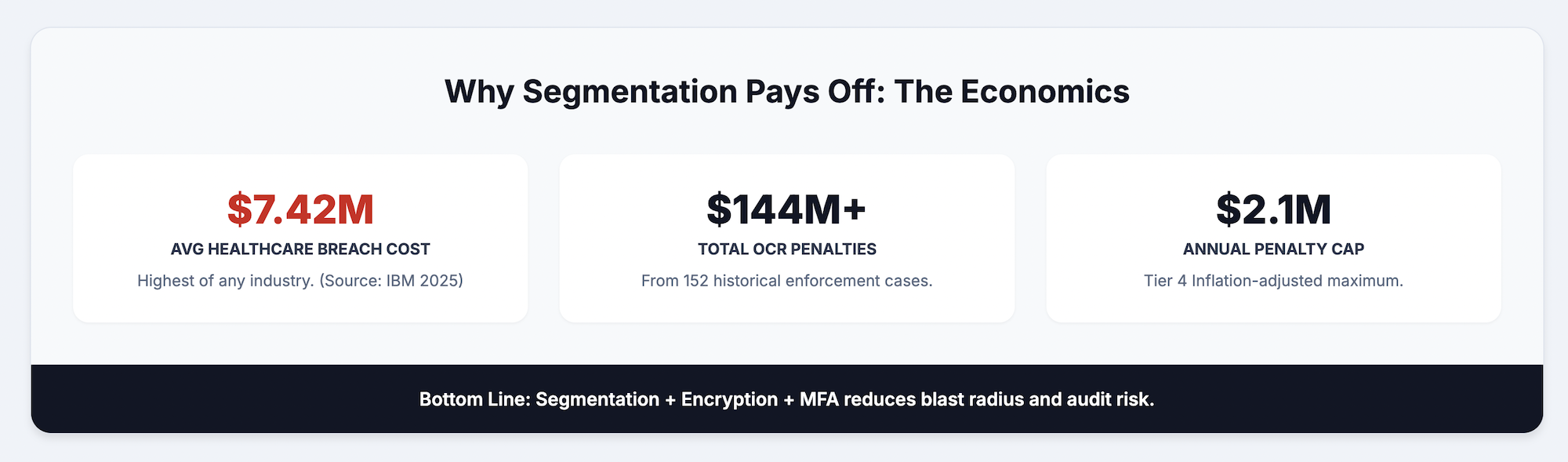
OCR enforces HIPAA violations through tiered civil monetary penalties ranging from $100 to $50,000 per violation, with annual maximums reaching $1.5 million per violation category. Organizations also face breach notification requirements, potential criminal penalties for willful neglect, and significant reputational damage following publicized violations.
Yes. Small practices can achieve meaningful segmentation through VLAN configuration on managed switches and properly configured firewall rules. Cloud-based solutions and managed security services offer enterprise-grade protection without requiring significant capital investment in on-premises equipment.
Auditors typically request network diagrams showing segmentation architecture, current risk assessments, access control policies, firewall rule sets with change documentation, encryption configurations, penetration test results, and evidence of regular security training and awareness programs.
See the power of IT GOAT.
The world’s most advanced cybersecurity platform catered specifically to your business’ needs.
Keep up to date with our digest of trends & articles.
By subscribing, I agree to the use of my personal data in accordance with IT GOAT Privacy Policy. IT GOAT will not sell, trade, lease, or rent your personal data to third parties.

Mitigate All Types of Cyber Threats
Experience the full capabilities of our advanced cybersecurity platform through a scheduled demonstration. Discover how it can effectively protect your organization from cyber threats.

IT GOAT: Threat Intel & Cyber Analysis
We are experts in the field of cybersecurity, specializing in the identification and mitigation of advanced persistent threats, malware, and exploit development across all platforms.

Protect Your Business & Operations
Exceptional performance in the latest evaluations, achieving 100% prevention rate and providing comprehensive analytic coverage, unmatched visibility, and near-instant detection of threats.
We use cookies to enhance site performance and user experience. Your data stays private — we don’t sell your information or share it with unrelated third parties. To find out more about the cookies we use, view our Privacy Policy.