Healthcare organizations face mounting pressure to protect patient data while maintaining seamless clinical operations—and your network infrastructure sits at the center of both challenges. A single misconfigured firewall or unencrypted connection can trigger devastating breaches, regulatory penalties, and loss of patient trust.
This guide breaks down the technical, physical, and administrative requirements for HIPAA-compliant network design, from initial risk assessment through ongoing monitoring and incident response. You’ll learn specific implementation steps, firewall configurations, encryption standards, and segmentation strategies that transform complex regulatory requirements into actionable network architecture decisions.

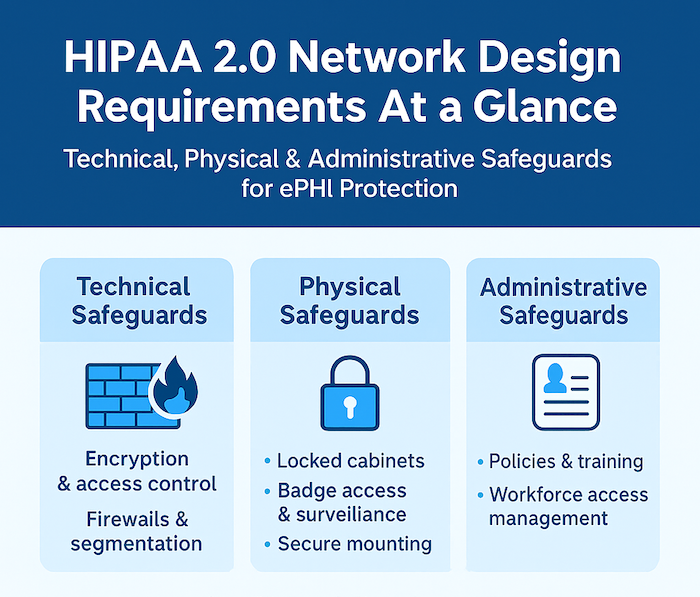
A HIPAA-compliant network design incorporates technical, physical, and administrative safeguards to protect electronic protected health information (ePHI). The framework requires network segmentation to isolate sensitive data, robust access controls including multi-factor authentication and role-based permissions, strong encryption for data in transit and at rest, properly configured firewalls, continuous monitoring systems, and strict physical security measures for all hardware handling patient information.
Protected Health Information (PHI) includes any individually identifiable health data—medical records, billing information, test results, and prescription details. When this information exists in electronic form, it becomes ePHI and falls under the HIPAA Security Rule’s network protection requirements. Healthcare organizations handle this data across interconnected systems daily, making network security the foundation of compliance and patient privacy protection.
Covered entities include healthcare providers who transmit health information electronically, health plans that pay for medical care, and healthcare clearinghouses that process health information. Hospitals, clinics, physician practices, pharmacies, insurance companies, and third-party billing services all fall into this category.
Business associates—vendors and service providers who access, process, or store PHI on behalf of covered entities—also carry full HIPAA compliance obligations, often alongside SOC 2 requirements for demonstrating security controls to their clients. IT managed service providers, cloud hosting companies, medical billing firms, and software vendors all qualify as business associates. Even subcontractors working with business associates inherit compliance requirements through the chain of responsibility.
The 2013 HIPAA Omnibus Rule expanded liability significantly, making business associates directly accountable for Security Rule violations. Your network design affects not just your own compliance posture but potentially dozens of partner organizations depending on your role in the healthcare ecosystem.

The HIPAA Security Rule organizes compliance requirements into three interconnected categories that work together to protect ePHI. Each category addresses different aspects of network security, creating a comprehensive defense-in-depth strategy.
Physical safeguards control access to facilities and hardware containing ePHI. Data centers require locked server rooms with badge access systems, surveillance cameras, and visitor logs that document every entry.
Network equipment like switches, routers, and firewalls requires secure mounting in locked cabinets with limited access granted only to authorized IT personnel. Workstations in clinical areas need positioning that prevents unauthorized viewing of patient data on screens.
Technical safeguards represent the actual technology controls embedded in your network infrastructure. Access controls ensure unique user IDs for every person, automatic logoff after inactivity periods, and encryption for authentication credentials.
Audit controls create detailed logs of who accessed what data, when, and from which device or location. Integrity controls verify that ePHI hasn’t been altered or destroyed inappropriately through checksums and version tracking. Transmission security protects data moving across networks through encryption protocols like TLS 1.2 or higher for all communications containing patient information.
Administrative safeguards establish the policies, procedures, and training that govern how your organization manages network security. Security management processes include regular risk analyses, documented risk management strategies, and sanction policies for employees who violate security protocols.
Workforce training ensures every employee understands their role in protecting patient data and recognizes common security threats. Information access management defines which roles can access specific types of ePHI, implementing the principle of least privilege across your network architecture.
Building a compliant network from the ground up follows a structured methodology that addresses both immediate security needs and long-term scalability. The process typically spans several months depending on organizational complexity and existing infrastructure.
Start by cataloging every device, application, and data repository that touches ePHI. This inventory includes servers, workstations, mobile devices, network equipment, cloud services, and even medical devices with network connectivity. Document where ePHI resides, how it flows through systems, and who accesses it.
The risk analysis identifies vulnerabilities in current systems—outdated encryption, weak authentication, unpatched software, or inadequate access controls. You’ll evaluate the likelihood and potential impact of threats ranging from ransomware attacks to insider data theft.
Network segmentation divides your infrastructure into isolated zones based on data sensitivity and functional requirements. A typical healthcare network includes separate segments for clinical systems with ePHI, administrative systems with limited patient data, guest networks for visitors, and quarantine zones for medical devices.
Trust zones establish security boundaries with different access requirements. The clinical zone hosting your EHR system demands the strictest controls, while the administrative zone for email and office applications requires moderate protection.
Enterprise-grade firewalls provide the security perimeter for your network segments. Next-generation firewalls offer deep packet inspection, application-level filtering, and integrated threat intelligence that blocks known malicious traffic.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) add another security layer by monitoring network traffic for suspicious patterns. IDS alerts your team to potential threats, while IPS can automatically block attacks in real-time.
All ePHI moving across your network requires encryption using protocols like TLS 1.2 or higher. This includes web traffic to cloud applications, database connections, file transfers, and internal communications between servers. VPN connections protect remote access sessions, encrypting the entire data stream from endpoint to network.
Data at rest encryption protects ePHI stored on servers, databases, and backup systems using AES-256 or equivalent standards. Full-disk encryption secures workstations and laptops against theft, while database-level encryption adds granular protection for patient records.
Multi-factor authentication (MFA) requires users to provide two or more verification methods—typically a password plus a mobile authenticator code or biometric scan. This dramatically reduces the risk of compromised credentials leading to unauthorized ePHI access.
Role-based access control (RBAC) assigns permissions based on job functions rather than individuals. A physician role might access full patient records, while a billing specialist role sees only demographic and payment information.
Written policies document your network security standards, acceptable use guidelines, incident response procedures, and consequences for violations. Regular training sessions ensure staff understand both the “what” and “why” of security practices.
Cover topics like recognizing phishing attempts, proper password management, secure handling of mobile devices, and reporting procedures for suspected security incidents. Training transforms technical controls into practical behaviors that protect patient data.
Penetration testing simulates real-world attacks against your network to identify exploitable vulnerabilities before malicious actors find them. Compliance audits verify that implemented controls actually function as designed and meet HIPAA requirements. Internal audits catch issues early, while external audits by qualified assessors provide independent validation.
Firewalls serve as the primary gatekeepers controlling traffic flow between network segments and to the internet. HIPAA doesn’t mandate specific firewall products, but the Security Rule requires organizations to implement firewall protection that’s reasonable and appropriate for their risk profile.
Modern firewalls perform stateful packet inspection, tracking the state of network connections and making decisions based on context rather than just individual packets. Application control takes this further by identifying specific applications generating traffic, not just port numbers.
You can allow general web browsing while blocking risky file-sharing applications, or permit approved cloud services while denying unauthorized shadow IT tools. This granular control prevents data exfiltration through seemingly legitimate network traffic.
Integrated intrusion prevention actively blocks attacks detected in network traffic. When the system identifies a pattern matching a known exploit or malware signature, it drops those packets automatically rather than just alerting administrators.
Threat intelligence feeds provide real-time updates about newly discovered vulnerabilities and active attack campaigns. Your firewall receives regular signature updates that recognize the latest threats, maintaining protection against evolving attack techniques.
Healthcare networks operate 24/7, making firewall downtime unacceptable, requiring continuous network monitoring to maintain availability. High availability configurations use redundant firewall pairs that automatically failover if the primary device fails.
Comprehensive logging captures every connection attempt, policy violation, and security event for compliance documentation. Logs feed into your Security Information and Event Management (SIEM) system for correlation with other security data sources.
Traditional network security assumed everything inside the network perimeter was trustworthy. Modern zero-trust architecture abandons this assumption, requiring verification for every access request regardless of network location.
The Internet of Medical Things (IoMT) encompasses connected medical devices like infusion pumps, imaging equipment, and patient monitors. Many devices run outdated operating systems that can’t be easily updated, creating significant security vulnerabilities when connected to networks handling ePHI.
Virtual LANs (VLANs) create logical network segments on shared physical infrastructure. A typical design includes separate VLANs for:
Each VLAN operates as an isolated broadcast domain with controlled routing between segments. Guest networks provide internet access for visitors and personal devices without any path to internal systems containing ePHI.
Microsegmentation takes network isolation to the individual workload level, creating security policies for specific applications or even individual virtual machines. This approach limits lateral movement—if an attacker compromises one system, they can’t easily pivot to other systems even within the same network segment.
Software-defined perimeters (SDP) extend zero-trust principles to network access, making resources invisible until after authentication. Users authenticate first, then gain access only to specific resources they’re authorized to use.
Older medical devices that can’t support modern security protocols require special isolation strategies. Device-specific VLANs with strict firewall rules allow medical equipment to communicate only with their management servers and nothing else.
Network access control systems can automatically quarantine unknown or non-compliant devices attempting to connect. Regular vulnerability scanning identifies security weaknesses in legacy equipment, though patching options may be limited.
Strong cryptography and robust identity controls form the technical foundation of ePHI protection. Encryption renders data unreadable to unauthorized parties, while access management ensures only the right people can decrypt and view patient information.
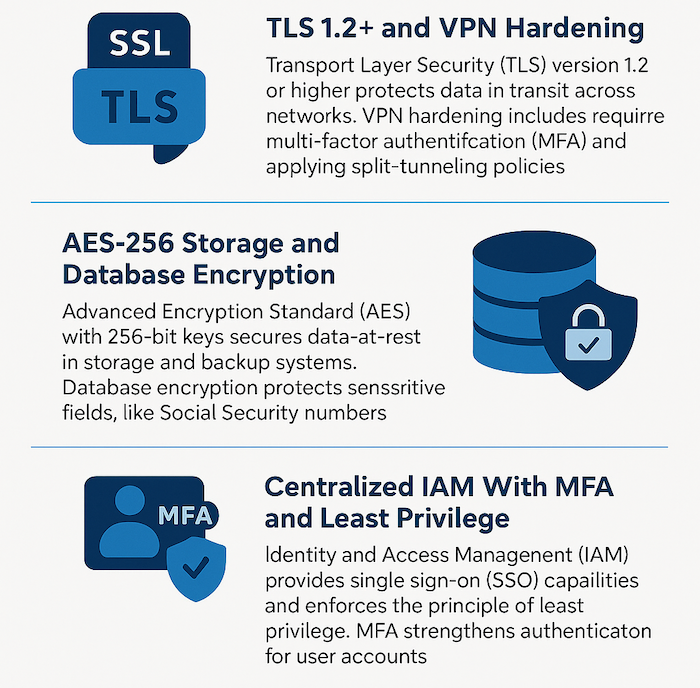
Transport Layer Security (TLS) version 1.2 or higher protects data in transit across networks. Older protocols like SSL and TLS 1.0/1.1 contain known vulnerabilities and fail to meet current security standards.
Virtual Private Networks (VPN) create encrypted tunnels for remote access to internal systems. VPN hardening includes requiring MFA before connection, implementing split-tunneling policies that route only corporate traffic through the VPN, and automatic disconnection after inactivity periods.
Advanced Encryption Standard with 256-bit keys (AES-256) represents the current gold standard for data-at-rest encryption. This encryption protects databases, file servers, and backup systems—if storage media is stolen or improperly disposed of, the encrypted data remains unreadable without proper decryption keys.
Database encryption can operate at multiple levels. Transparent data encryption protects entire databases, while column-level encryption secures specific sensitive fields like Social Security numbers.
Identity and Access Management (IAM) systems provide centralized control over user authentication and authorization. Single sign-on (SSO) allows users to authenticate once and access multiple systems without repeated login prompts.
Least privilege access means users receive only the minimum permissions required for their job functions. Regular access reviews identify and remove unnecessary permissions that accumulate over time.
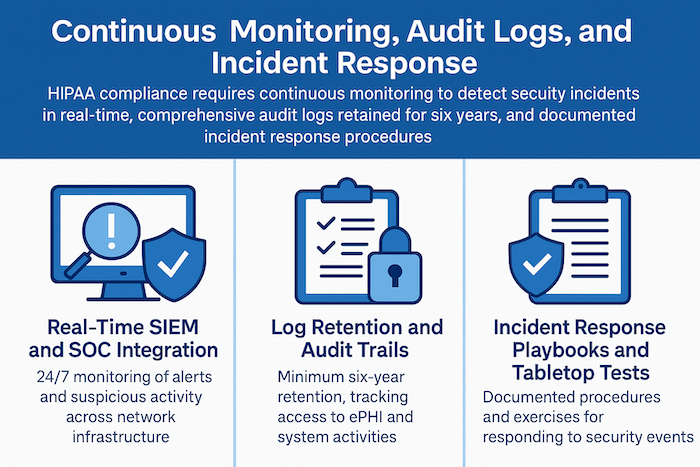
HIPAA compliance isn’t a one-time achievement but an ongoing operational requirement. Continuous monitoring detects security incidents in real-time, while comprehensive logging provides the evidence trail needed for compliance audits and breach investigations.
Security Information and Event Management (SIEM) systems aggregate logs from across your network infrastructure—firewalls, servers, applications, and endpoints. Advanced analytics correlate events from different sources to detect complex attack patterns that would be invisible when examining individual systems.
Security Operations Center (SOC) teams monitor SIEM alerts 24/7, investigating suspicious activity and responding to confirmed incidents. For many healthcare organizations, partnering with a managed security service provider offers SOC capabilities without the cost of building an in-house security team.
HIPAA requires retaining audit logs for at least six years from creation or last use. Logs document who accessed ePHI, what actions they performed, when access occurred, and from which systems.
Regular log reviews identify unusual access patterns that might indicate insider threats or compromised accounts. Automated alerts flag high-risk activities like bulk data exports, access to records of VIP patients, or login attempts outside normal business hours.
Incident response playbooks document step-by-step procedures for handling different types of security events—from malware infections to suspected data breaches. Clear playbooks reduce response time and ensure consistent handling across different incidents and team members.
Tabletop exercises simulate security incidents in a low-pressure environment, allowing teams to practice response procedures and identify gaps in plans or capabilities. Exercises might simulate ransomware attacks, insider data theft, or natural disasters affecting data center operations.
Building and maintaining HIPAA-compliant network infrastructure demands specialized expertise that extends beyond general IT knowledge. The technical requirements combine with complex regulatory obligations, creating challenges for organizations trying to manage compliance internally.
IT GOAT delivers comprehensive managed IT services specifically designed for healthcare organizations navigating HIPAA compliance requirements. Our U.S.-based security operations center provides 24/7 monitoring, our certified professionals understand both the technical and regulatory aspects of healthcare IT, and our proactive approach prevents security incidents before they impact your operations.
Book an appointment to discuss your specific HIPAA network design requirements and learn how IT GOAT’s healthcare-focused managed services can provide the expertise, monitoring, and support your organization needs to maintain compliance confidently.
Implementation costs vary significantly based on organization size, existing infrastructure condition, and complexity of clinical workflows. Small practices might invest $20,000-$50,000 for basic compliance, while larger multi-location organizations could spend $200,000+ for comprehensive enterprise solutions. Ongoing costs for monitoring, maintenance, and managed security services typically range from $2,000-$20,000 monthly depending on scope and service levels.
Cloud-based networks can achieve full HIPAA compliance when properly configured with appropriate security controls and Business Associate Agreements with cloud providers. Major platforms like AWS, Azure, and Google Cloud offer HIPAA-compliant services, though organizations remain responsible for configuring encryption, access controls, and monitoring correctly.
Organizations typically conduct formal risk analyses at least annually, with additional assessments required after significant network changes, security incidents, or when adopting new technologies. Continuous monitoring supplements periodic formal assessments by identifying emerging threats and vulnerabilities in real-time.
Zero-trust provides strong security foundations but doesn’t automatically guarantee HIPAA compliance, which requires specific administrative, physical, and technical safeguards beyond network architecture. Organizations still need formal policies, workforce training, Business Associate Agreements, risk analyses, and comprehensive audit logging.
See the power of IT GOAT.
The world’s most advanced cybersecurity platform catered specifically to your business’ needs.
Keep up to date with our digest of trends & articles.
By subscribing, I agree to the use of my personal data in accordance with IT GOAT Privacy Policy. IT GOAT will not sell, trade, lease, or rent your personal data to third parties.

Mitigate All Types of Cyber Threats
Experience the full capabilities of our advanced cybersecurity platform through a scheduled demonstration. Discover how it can effectively protect your organization from cyber threats.

IT GOAT: Threat Intel & Cyber Analysis
We are experts in the field of cybersecurity, specializing in the identification and mitigation of advanced persistent threats, malware, and exploit development across all platforms.

Protect Your Business & Operations
Exceptional performance in the latest evaluations, achieving 100% prevention rate and providing comprehensive analytic coverage, unmatched visibility, and near-instant detection of threats.
We use cookies to enhance site performance and user experience. Your data stays private — we don’t sell your information or share it with unrelated third parties. To find out more about the cookies we use, view our Privacy Policy.