A single ransomware attack can cost a manufacturing company more than $6 million when you add up ransom payments, production losses, legal fees, and long-term business damage. That figure keeps climbing as attackers increasingly target manufacturers who face enormous pressure to pay quickly and restore operations.
This guide breaks down exactly where those recovery dollars go, why manufacturing downtime costs more than other industries, and what proactive steps can dramatically reduce your exposure.

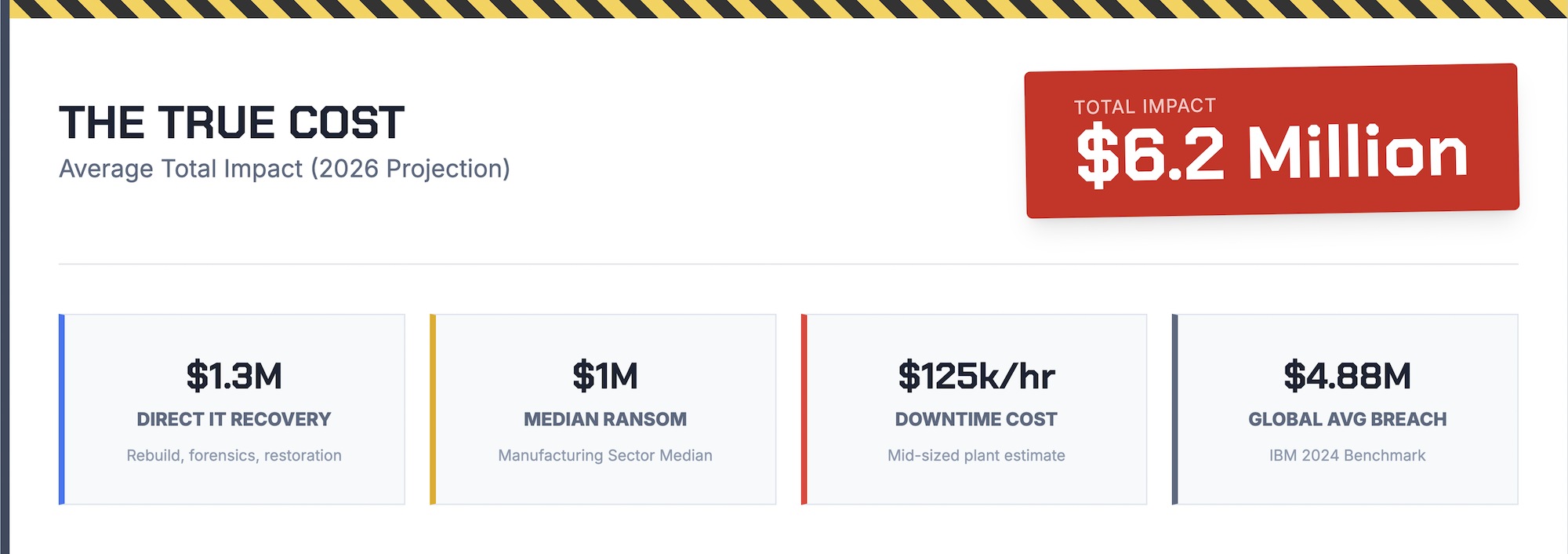
Ransomware recovery for manufacturing companies averages $1.3 million in direct costs, excluding ransom payments. When you factor in ransom payments, legal fees, lost revenue, and long-term business impact, total costs can climb well past $6 million for larger operations. Manufacturing sits among the highest-risk sectors because attackers know production-dependent businesses face enormous pressure to pay quickly and get lines running again.
The term “ransomware recovery cost” covers every expense involved in returning to normal operations. Think IT forensics, system rebuilding, lost production revenue, legal counsel, regulatory compliance work, and the harder-to-measure damage to customer relationships. For manufacturers specifically, costs compound fast because downtime stops physical production lines that simply cannot catch up later.
What makes manufacturing such an attractive target? The sector runs on interconnected systems where operational technology meets traditional IT infrastructure. A single compromised endpoint can cascade through production networks and halt entire facilities within hours.
Knowing where recovery dollars actually go helps manufacturers build realistic budgets and spot areas where proactive investment pays off.
Rebuilding compromised networks represents the most predictable cost category. This work includes replacing infected hardware, restoring software from backups, and reconfiguring security systems to prevent reinfection.
Many manufacturers discover their backups were also compromised or were never properly tested. When clean backups don’t exist, restoration becomes exponentially more expensive and time-consuming.
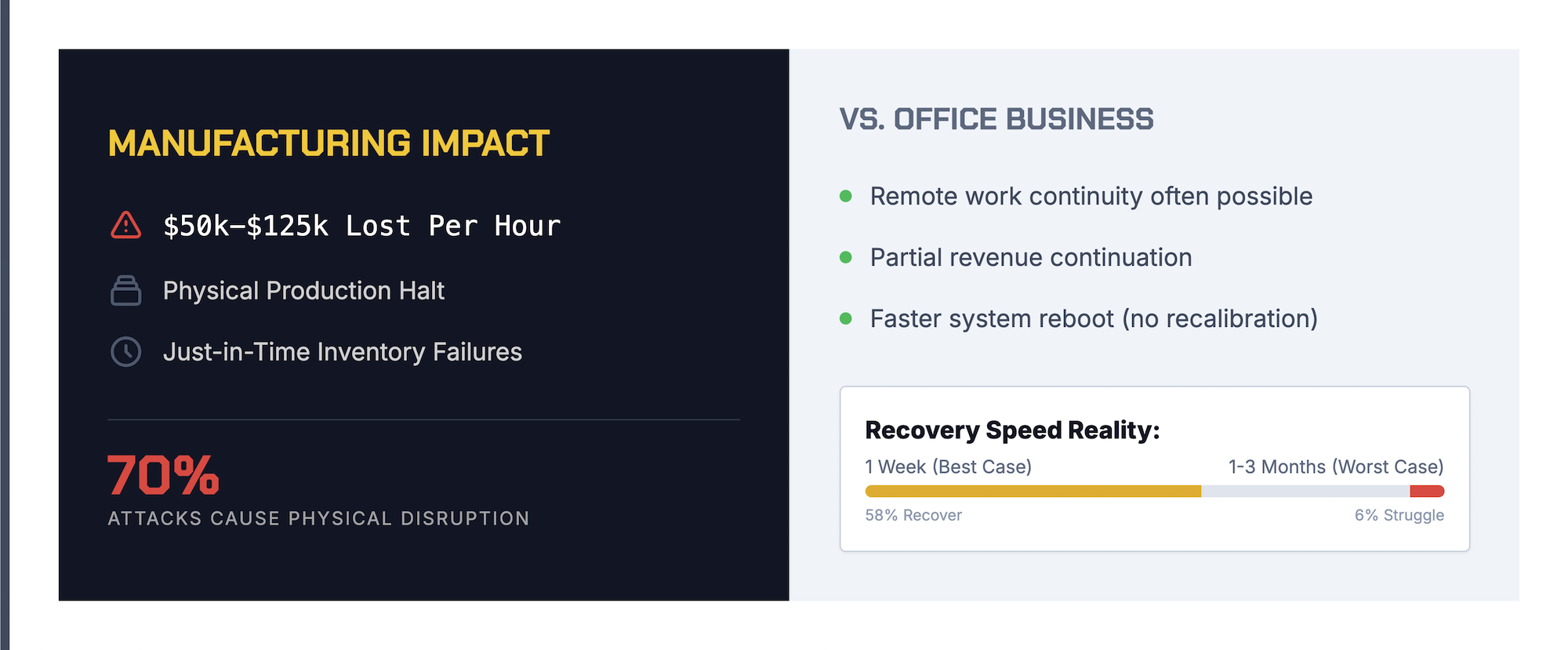
For most manufacturers, downtime is the largest cost component and the one that escalates fastest. A mid-sized production facility might lose anywhere from $50,000 to $125,000 per hour, depending on products and contracts.
Unlike office-based businesses that can partially operate remotely, manufacturing requires physical equipment running in physical facilities. There’s no workaround when production lines stop.
Attorney fees start accumulating immediately after an incident. Manufacturers face mandatory breach notification requirements, potential regulatory investigations, and sometimes class action exposure if customer or employee data was compromised.
Companies operating under frameworks like CMMC or handling data subject to GDPR face additional compliance obligations that increase legal complexity.
This cost is harder to quantify but often substantial. Customers who depend on reliable supply chains may shift to competitors after a production halt, even if the manufacturer recovers quickly. Long-term contract negotiations become more difficult when potential partners research your incident history.
External cybersecurity experts are typically essential for proper incident response. Forensic specialists investigate how attackers gained access, determine the full scope of compromise, and verify that systems are clean before reconnection.
Forensic investigations often reveal additional compromised systems that internal teams missed. While expensive, this expertise prevents the costly mistake of restoring operations on still-infected infrastructure.
Manufacturing downtime carries unique financial consequences that don’t apply to service-based or office-centric businesses.
| Factor | Manufacturing Impact | Office-Based Business Impact |
|---|---|---|
| Production halt | Complete revenue stoppage | Partial operations continue |
| Supply chain | Contractual penalties and partner disruption | Minimal downstream effect |
| Equipment restart | Complex calibration and safety checks | Simple system reboot |
| Inventory | Perishable materials and storage costs | Not applicable |
Just-in-time production models mean manufacturers often carry minimal inventory buffers. When production stops, customer orders go unfilled within days rather than weeks.
OT systems, which are the industrial control systems that run production equipment, require specialized expertise to restore safely. You can’t simply reimage an industrial controller the way you would a laptop. Improper restoration can damage expensive equipment or create safety hazards.
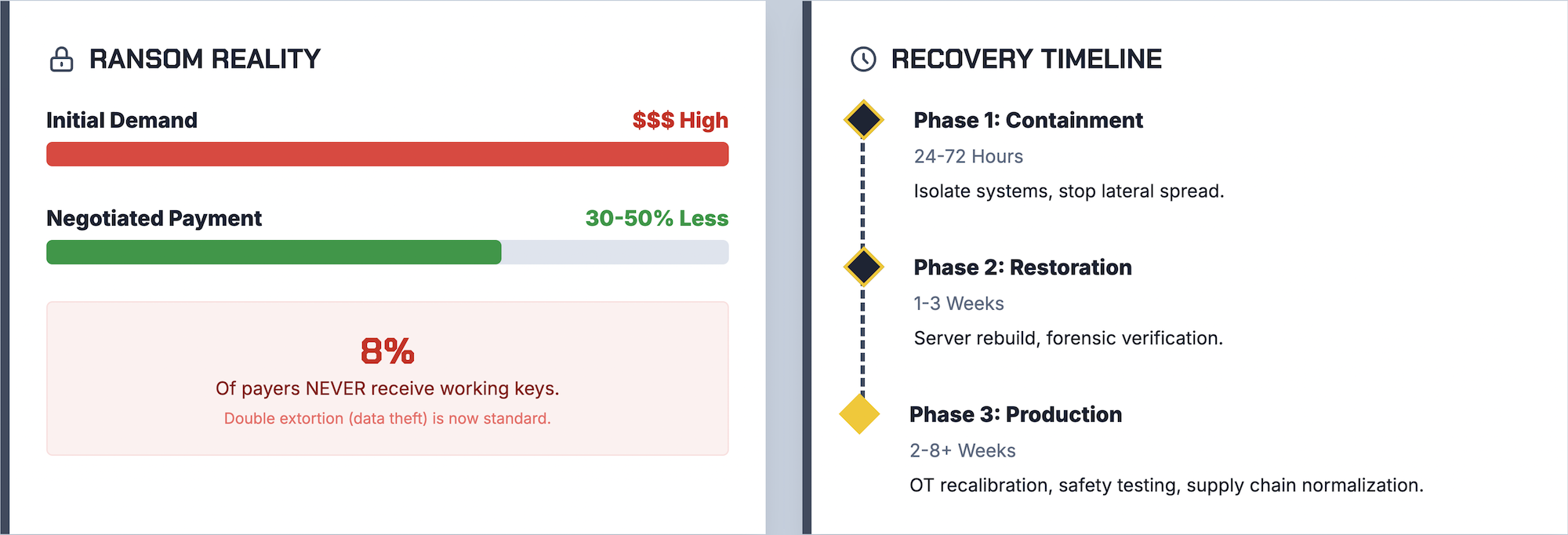
Ransom demands targeting manufacturers have increased significantly, with median payments now reaching approximately $1 million. However, the decision to pay involves complex considerations beyond the dollar amount.
Attackers typically demand more than companies ultimately pay. Negotiation is common, and many organizations successfully reduce demands by 30-50% through professional negotiators or by demonstrating limited ability to pay.
The gap between demand and payment reflects a practical reality: attackers want money, not prolonged standoffs. They often prefer a smaller guaranteed payment over a larger demand that results in nothing.
Several factors shape whether a company pays and how much:
Payment doesn’t guarantee recovery. Approximately 8% of organizations that pay never receive working decryption keys, and even successful decryption often leaves systems unstable.
Recovery timelines vary dramatically based on preparation, attack severity, and available resources. Even well-prepared organizations typically require weeks to return to full capacity.
The first 24-72 hours focus on stopping the spread. This means isolating infected systems, identifying the attack vector, and preventing additional encryption or data theft.
During this phase, production is typically completely halted. Rushing to restore systems before containment is complete often results in reinfection and extended downtime.
Rebuilding servers, validating backups, and restoring applications typically takes one to three weeks for organizations with solid backup infrastructure. Without clean backups, this phase can extend to months.
Each restored system requires verification before reconnection. Attackers often leave persistent access mechanisms that survive initial cleanup attempts.
Returning to normal production capacity often takes longer than IT restoration alone. OT systems require recalibration, safety validation, and testing before resuming full-speed production.
Approximately 58% of manufacturers recover within a week, while 6% require one to three months. The difference usually comes down to preparation, specifically whether incident response plans and backup systems were in place before the attack.
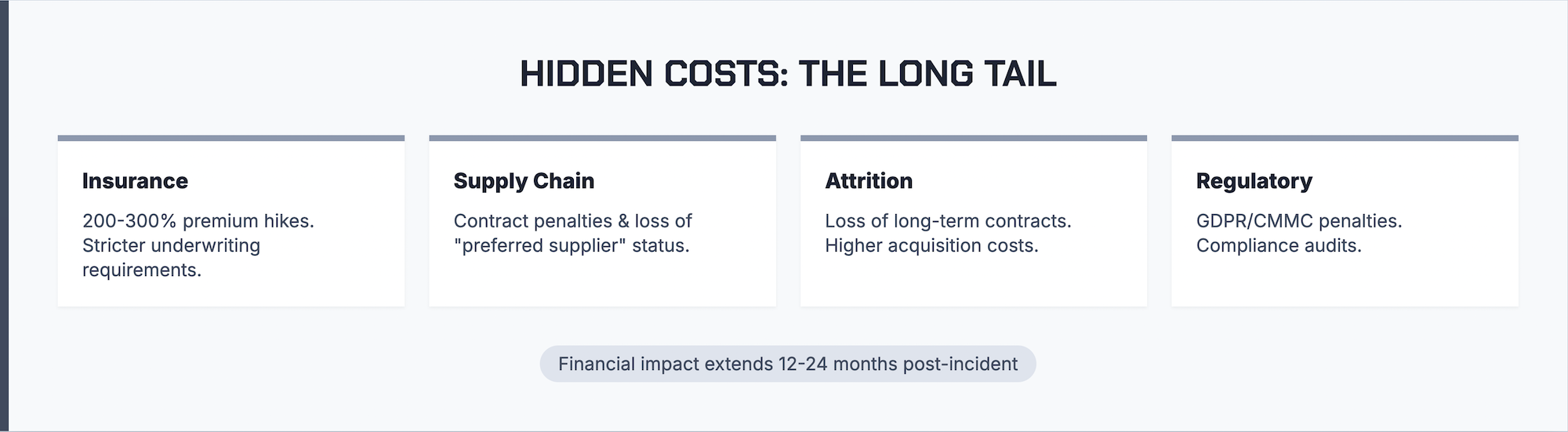
Many manufacturers underestimate total impact because they focus only on immediate recovery expenses. Several cost categories emerge months after the incident appears resolved.
Your downtime affects your customers’ operations. Contractual penalties for missed deliveries, expedited shipping costs to catch up, and damaged partner relationships all contribute to total impact. Some customers may invoke force majeure clauses or seek alternative suppliers permanently.
Post-incident insurance renewals often bring significantly higher premiums, sometimes 200-300% increases. Insurers may also impose new security requirements or reduce coverage limits. Some manufacturers discover their policies excluded key costs they assumed were covered.
Customer attrition following a publicized incident can continue for years. Procurement teams increasingly evaluate supplier cybersecurity posture, and a breach history becomes a competitive disadvantage. New customer acquisition costs also increase when prospects research your company and find incident reports.
Depending on your industry and the data involved, regulatory bodies may impose fines or require mandatory security improvements. Defense contractors, food manufacturers, and companies handling personal data face particularly stringent requirements. Post-incident audits often reveal pre-existing compliance gaps that compound penalties.
The threat landscape facing manufacturers continues evolving. Attackers have refined their tactics specifically for industrial targets, making awareness of current trends essential for effective defense.
Key developments include:
Sophos research indicates that while manufacturers are blocking more attacks before encryption, successful incidents still result in significant costs and extended recovery periods.
Proactive investment in prevention and preparation directly reduces recovery costs when incidents occur.
24/7 Security Operations Center monitoring enables early threat detection before attacks escalate to encryption. Many ransomware incidents show warning signs days or weeks before the final payload deploys. Early detection can mean the difference between a contained security event and a full production shutdown.
Standard network-connected backups often fail during ransomware attacks because they’re encrypted along with primary systems. Air-gapped backups are physically isolated from networks, while immutable backups cannot be modified or deleted. Both provide genuine recovery options when standard backups fail.
Regular backup testing is equally important. Untested backups frequently fail when needed most.
Documented procedures, assigned roles, and practiced playbooks enable faster, more organized response. Organizations with tested incident response plans recover significantly faster than those improvising during a crisis.
The plan typically includes communication templates, vendor contact information, and decision trees for common scenarios.
Identifying and fixing security weaknesses before attackers exploit them reduces breach likelihood significantly. Both IT and OT environments require assessment, as attackers increasingly target the intersection between these systems. Vulnerability assessments typically occur at least quarterly, with additional scans after significant infrastructure changes.
Human error remains a primary attack vector in manufacturing environments. Regular training helps employees recognize phishing emails, suspicious requests, and social engineering tactics. Training works best as an ongoing effort rather than an annual event, with simulated phishing exercises to reinforce awareness.
Prevention costs far less than recovery, typically by a factor of 10 or more. The manufacturers who weather ransomware incidents with minimal impact share common characteristics: proactive monitoring, tested backups, documented response plans, and ongoing security partnerships.
For manufacturers seeking security-focused managed IT services that understand both IT and OT environments, schedule a consultation with IT GOAT to discuss your specific risk profile and protection options.
The 3-2-1 rule means maintaining three copies of your data on two different media types, with one copy stored offsite. This approach helps manufacturers recover without paying ransom because the offsite copy, ideally air-gapped or immutable, remains protected from network-based attacks.
There’s no universal answer. While payment doesn’t guarantee data return and may encourage future attacks, some companies face existential pressure when downtime threatens business survival. The decision typically involves legal counsel, insurance carriers, and careful assessment of alternatives.
Coverage varies significantly by policy. Many policies exclude certain costs like reputational damage or impose sub-limits on ransom payments. Some require specific security controls to have been in place before the incident for coverage to apply. Reviewing policy details with your broker before an incident is essential.
A starting framework involves three calculations: daily revenue loss from complete production stoppage, estimated IT rebuild costs based on system complexity, and potential contractual penalties for failing to meet customer obligations. This baseline helps justify appropriate security investments.
See the power of IT GOAT.
The world’s most advanced cybersecurity platform catered specifically to your business’ needs.
Keep up to date with our digest of trends & articles.
By subscribing, I agree to the use of my personal data in accordance with IT GOAT Privacy Policy. IT GOAT will not sell, trade, lease, or rent your personal data to third parties.

Mitigate All Types of Cyber Threats
Experience the full capabilities of our advanced cybersecurity platform through a scheduled demonstration. Discover how it can effectively protect your organization from cyber threats.

IT GOAT: Threat Intel & Cyber Analysis
We are experts in the field of cybersecurity, specializing in the identification and mitigation of advanced persistent threats, malware, and exploit development across all platforms.

Protect Your Business & Operations
Exceptional performance in the latest evaluations, achieving 100% prevention rate and providing comprehensive analytic coverage, unmatched visibility, and near-instant detection of threats.
We use cookies to enhance site performance and user experience. Your data stays private — we don’t sell your information or share it with unrelated third parties. To find out more about the cookies we use, view our Privacy Policy.