Firewalls examine every packet of data entering and leaving your network, then decide what gets through based on rules you configure. For small businesses, these rules determine whether you block ransomware at the perimeter or let it walk straight through your front door.
Most small-business networks start with overly permissive rules that allow everything by default—the equivalent of leaving all your doors unlocked and hoping criminals don’t notice. This guide covers the specific firewall rules, network segmentation strategies, and ongoing management practices that protect your business without disrupting daily operations.

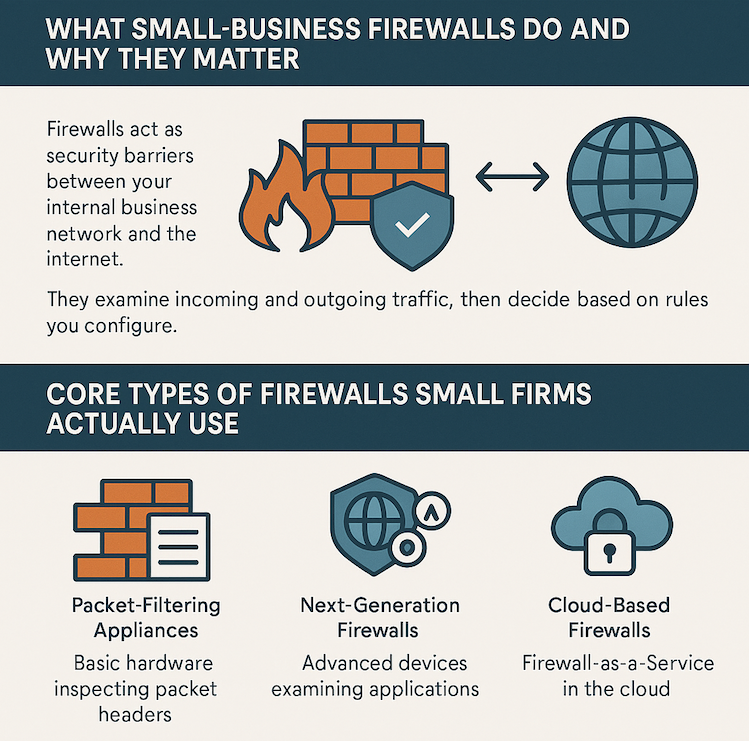
Firewalls act as security barriers between your internal business network and the internet. They examine incoming and outgoing traffic, then decide what gets through based on rules you configure. For small businesses, firewalls provide the first line of defense against malware, ransomware, data breaches, and unauthorized access attempts.
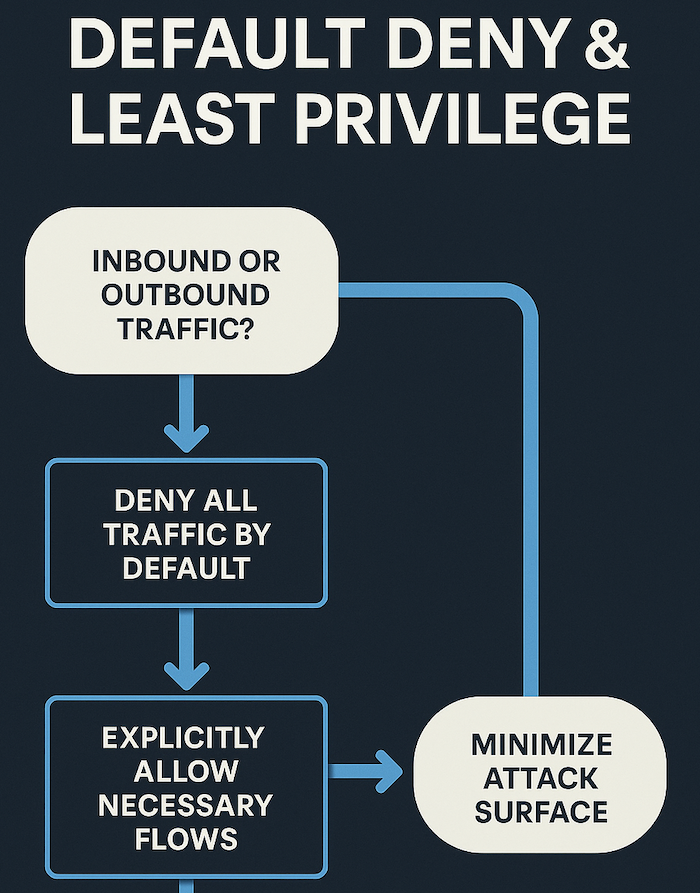
The most effective approach starts by blocking all traffic by default. From there, you explicitly allow only what your business operations actually require. This “default-deny” strategy prevents unknown threats from entering while giving you complete visibility into which applications and services your team uses day-to-day.
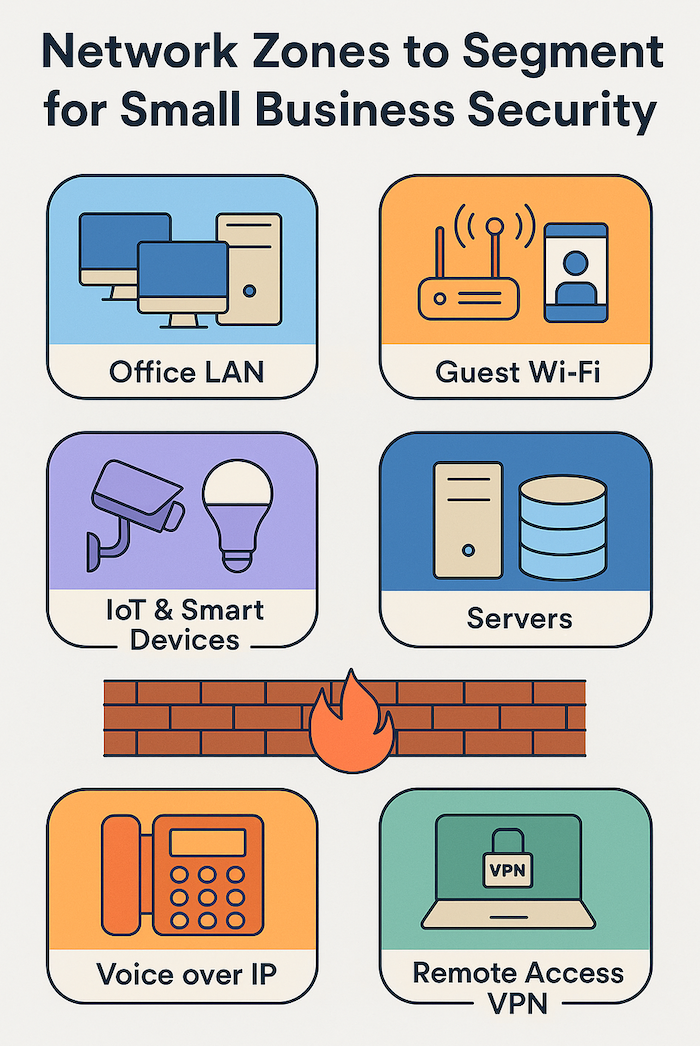
When configured properly, firewalls also enable network segmentation. This means separating your guest Wi-Fi from business systems, isolating sensitive data from general office traffic, and keeping different parts of your network from talking to each other unless they have a legitimate reason to do so.
Small and midsize businesses face different security scenarios than enterprises. Choosing the right firewall type depends on your specific situation, technical capabilities, and budget rather than chasing the most advanced features.
Basic hardware devices inspect packet headers—the source and destination IP addresses, ports, and protocols—then make simple allow or deny decisions. These work well for straightforward, single-site networks with limited applications and minimal regulatory requirements. You get low cost and simple management, though you’ll have limited visibility into what applications actually run and fewer security features like intrusion prevention.
Advanced appliances with deep packet inspection can identify applications regardless of which port they use. They detect threats using intrusion prevention systems (IPS), filter URLs, and tap into threat intelligence feeds. Next-generation firewalls fit growing businesses, multi-site operations, or regulated environments where you want granular control. The trade-off comes through higher upfront costs, ongoing licensing fees, and more complex management.
Firewall-as-a-Service (FWaaS) applies security policies in the cloud, protecting traffic from branches, remote workers, and cloud applications without routing everything through a central office. This model fits distributed teams and hybrid work particularly well. You get easy scaling and centralized management with consistent policies across all locations, though you’ll pay ongoing subscription costs and rely on your provider’s uptime.
Planning before you configure rules prevents security gaps, network outages, and shadow IT that bypasses your controls entirely. Start by documenting what systems you currently have, what business applications you actually use, and how traffic flows between different parts of your network.
Replace default administrator credentials with strong, unique passwords and turn on multi-factor authentication (MFA) for anyone who can modify firewall settings. Update firmware to patch known vulnerabilities that attackers actively exploit. Disable unused services and any management interfaces accessible from the internet. Always keep backup configurations before applying updates, and schedule firmware changes during planned maintenance windows.
Create a list of all business applications, the ports and protocols they use, and their dependencies like DNS, network time protocol (NTP), Active Directory, or single sign-on systems. Document who uses each application, where it lives—on-premises or in the cloud—and the required source and destination IP addresses. This inventory becomes your baseline for building rules that allow only necessary traffic.
Draw a topology showing your internet connection, WAN links, VLANs (virtual local area networks), subnets, Wi-Fi networks, servers, and cloud connectivity. Map typical traffic flows between zones, like office computers to SaaS applications, VoIP phones to your phone provider, or VPN users to internal file servers. This map helps you design proper segmentation and check that your rules match real-world traffic patterns.
Separating different functions means a security breach in one area won’t automatically spread across your entire network. Traffic between zones routes through your firewall for inspection rather than communicating directly.
Starting with a deny-all stance forces you to explicitly allow only necessary flows. This approach dramatically reduces your attack surface compared to allowing everything and trying to block the bad stuff implementing the principle of least privilege at the network level. For outbound traffic, restrict connections to essential services and destinations rather than giving blanket internet access.
Where your firewall supports it, bind rules to specific users, groups, or device tags instead of just IP addresses. Order rules from most specific to least specific so precise matches take precedence. Then regularly audit your rule set to remove unused entries and shadowed rules that never match because a broader rule above them handles the same traffic first.

Limiting what can reach your network from the internet protects you from the constant barrage of automated attacks. Prefer access through reverse proxies or VPN rather than directly exposing internal systems.
Publish only essential web applications via HTTPS with valid TLS certificates and strong encryption. Use a reverse proxy or web application firewall (WAF) for inspection, rate limiting, and protection against bots. Block legacy HTTP on port 80 entirely, or configure automatic redirects to HTTPS. Never expose administrative interfaces, database ports, or file shares directly to the internet.
Block internet access to administrative portals for your firewall, switches, servers, and other infrastructure. Require VPN connections with MFA or use dedicated management networks accessible only from secure locations. Restrict management sessions to specific administrator addresses, enable session timeouts, and log all administrative access. Management interfaces exposed to the internet face constant automated attacks and password guessing attempts.
If you run on-premises mail servers rather than using cloud email, allow SMTP on ports 25 or 587 only from known mail relays or spam filtering services. Permit secure IMAP or POP3 connections only from trusted networks or through VPN, never the unencrypted versions. Enforce TLS encryption and enable your firewall’s intrusion prevention to detect email-based attacks.
Balancing usability and security means allowing what your team actually needs while using application identification and category controls to block risky destinations. Modern firewalls can identify applications regardless of port, letting you create policies like “allow Salesforce” instead of “allow all HTTPS traffic.”
Force all computers to use your internal DNS servers or approved external resolvers, blocking connections to other DNS servers. This prevents malware from using DNS for command and control. Similarly, permit network time protocol (NTP) only to trusted time sources—accurate time matters for log correlation and security certificates—while blocking other time synchronization.
Apply category-based rules to reduce risk from malicious ads and preserve bandwidth for business operations. You might allow exceptions for marketing staff using policies tied to Active Directory groups, or apply time-of-day schedules if appropriate. Streaming video and social platforms consume significant bandwidth and introduce risks through user-generated content.
Turn on threat intelligence feeds that identify botnets, command-and-control servers, TOR exit nodes, and cryptocurrency mining pools. Consider geographic blocking for regions where you have no business operations—this immediately eliminates large volumes of automated attacks. Use your firewall’s ability to inspect encrypted connections and deploy URL filtering to stop phishing sites and malware delivery.
Modern work patterns require policies tuned for distributed operations while maintaining visibility and performance.
Microsoft publishes lists of IP addresses for Exchange Online, SharePoint, OneDrive, Teams, and other services. Use these vendor-provided lists or your firewall’s dynamic address objects to allow Microsoft 365 without manually tracking hundreds of addresses. Prioritize traffic to Teams for call quality, block legacy authentication that lacks MFA support, and skip SSL inspection for Microsoft’s recommended endpoints—they use certificate pinning that breaks when intercepted.
Allow SIP signaling to your phone provider’s servers, typically using port 5060 for unencrypted or 5061 for encrypted signaling. Permit RTP media on the UDP port ranges your vendor specifies, often something like 10000–20000, but only to your provider’s documented addresses. Apply Quality of Service (QoS) prioritization to prevent voice packets from competing with large file transfers.
Split tunneling sends general internet traffic directly from remote devices while routing corporate network access through the VPN. This improves performance by reducing load on your VPN and internet connection. Use application-based split rules when possible and implement DNS safeguards to prevent leaks of internal queries. For high-security roles like finance or executives, consider full tunnel where all traffic routes through your firewall.
Treating firewall rules as living configuration with traceability prevents security drift and maintains compliance over time.
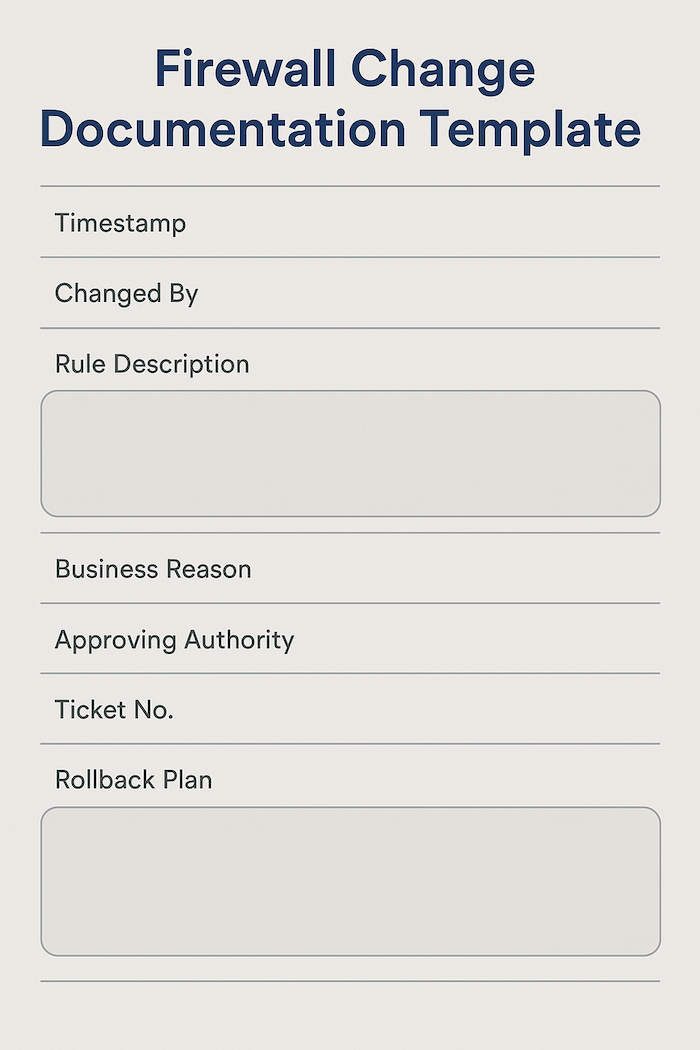
Document every firewall change using a standard format that captures the date, rule description, business reason, and approving authority. Include ticket numbers linking to your help desk system and maintain rollback plans for each change. This documentation proves essential during audits and helps future administrators understand why rules exist.
Run vulnerability scans after significant firewall changes to validate your security posture. Confirm you’ve closed unnecessary ports, eliminated management exposure on the internet, and properly configured encryption for published services. Fix any findings and retest to verify the corrections worked. Automate periodic scanning and configure alerts when new vulnerabilities appear.
Every quarter, schedule time to remove unused, temporary, or shadowed rules that no longer serve a purpose. Reconfirm business ownership for each rule and ask whether the application or service remains in use. Review logs for rule hit counts—rules with zero matches in 90 days might be candidates for removal—and investigate anomalies like unexpected traffic patterns.
Regular maintenance keeps your defenses current against evolving threats.
Mapping firewall controls to regulatory requirements and insurance questionnaires keeps evidence ready for audits and policy renewals.
Electronic protected health information (ePHI) lives in protected network zones with VPN or encrypted connections required for all access. Log all access attempts and restrict traffic to the minimum necessary for each role. The HIPAA Security Rule requires technical safeguards that firewalls directly support through access controls and transmission security.
Isolate your cardholder data environment from other networks using firewalls, restrict traffic to only required services, document all changes through formal processes, and perform quarterly vulnerability scans plus annual penetration tests. PCI DSS compliance prescribes specific firewall configurations that directly map to your rule set.
Demonstrate consistent change management, continuous monitoring and alerting, documented incident response, and appropriate controls over cloud firewalls and managed services. SOC 2 auditors examine whether you follow your documented policies, making process consistency as important as technical controls.
Prepare answers and supporting evidence for common questions about MFA on administrative access and VPN, endpoint detection and response (EDR) deployment, patch management frequency, immutable backups, geographic or threat intelligence blocking, and log retention periods. Insurers increasingly require specific security controls before offering coverage or competitive rates.
Choosing between self-management and partnering with an MSP depends on your risk tolerance, internal technical skills, and budget.
Self-managing firewalls carries lower recurring costs but requires significant time and expertise for rule design, ongoing tuning, log analysis, and threat response. Partnering with an MSP or MSSP (Managed Security Service Provider) provides predictable monthly fees, access to specialized expertise, and faster response times. A hybrid approach—where you maintain policy ownership while the MSP handles monitoring and implements approved changes—often balances control and capability effectively.
If your business requires continuous monitoring, alert triage, and rapid response to security events, partnering with an MSP or deploying a Security Information and Event Management (SIEM) system with on-call staff becomes practical. Define clear service level agreements for response times and establish escalation paths for critical incidents.
Partnering with experienced professionals for firewall management ensures your business stays protected without overwhelming your internal team. Expert configuration, proactive monitoring, and ongoing optimization deliver security outcomes that fit small-business budgets. Book a consultation to assess your current firewall setup and identify improvement opportunities that reduce risk and support business growth.
Expect to invest a few hundred to several thousand dollars for a single-site NGFW appliance, plus annual licenses for intrusion prevention, URL filtering, threat intelligence, and vendor support. Multi-site deployments or high-availability configurations increase costs proportionally. Include setup time, staff training, and ongoing management effort or MSP fees in your total cost calculation—the appliance price represents only part of the true investment.
Open-source platforms like pfSense or OPNsense can provide robust security when properly configured, hardened, and maintained by skilled technical staff. You’ll invest more time in setup and ongoing management with limited commercial support options, but gain lower costs and greater configuration flexibility. Many businesses successfully run open-source firewalls, though they typically have dedicated IT staff with networking and security expertise.
Configure health checks that monitor each internet connection’s availability and speed, then create routing rules with weighted paths for primary and secondary connections. Set failover triggers based on packet loss or latency thresholds, and enable session persistence so existing connections survive the switchover when possible. Some next-generation firewalls support per-application steering that automatically routes latency-sensitive traffic like VoIP over the best-performing link.
Adopt centralized management platforms that push standardized templates to all locations from a single console. Define base policies covering default-deny rules, outbound controls, logging standards, and common application access, then layer site-specific overrides for local servers or unique requirements. Use zero-touch provisioning for new branches where devices automatically download their configuration when first connected, and audit configuration drift regularly to catch manual changes that deviate from standards.
See the power of IT GOAT.
The world’s most advanced cybersecurity platform catered specifically to your business’ needs.
Keep up to date with our digest of trends & articles.
By subscribing, I agree to the use of my personal data in accordance with IT GOAT Privacy Policy. IT GOAT will not sell, trade, lease, or rent your personal data to third parties.

Mitigate All Types of Cyber Threats
Experience the full capabilities of our advanced cybersecurity platform through a scheduled demonstration. Discover how it can effectively protect your organization from cyber threats.

IT GOAT: Threat Intel & Cyber Analysis
We are experts in the field of cybersecurity, specializing in the identification and mitigation of advanced persistent threats, malware, and exploit development across all platforms.

Protect Your Business & Operations
Exceptional performance in the latest evaluations, achieving 100% prevention rate and providing comprehensive analytic coverage, unmatched visibility, and near-instant detection of threats.
We use cookies to enhance site performance and user experience. Your data stays private — we don’t sell your information or share it with unrelated third parties. To find out more about the cookies we use, view our Privacy Policy.